Ready’s processes for messaging and file transfer/storage are based on the proven Signal protocol and, thus, are secure, transparent, and sophisticated.
It should be emphasized that the following descriptions are simplified versions of the actual algorithms/protocols.
Mutually Authenticate Conversation Partners (with the Extended Triple Diffie-Hellman Key Exchange Protocol)
The fundamentals of secured communication are that the messages go to the intended recipient and that the conversation itself is closed to outsiders. Ready fulfills both of these requirements by using the Extended Triple Diffie-Hellman key exchange protocol at the start of any conversation.
- All users publish their identity, signed keys, and signatures to Ready’s key servers.
.png?table=block&id=37744d48-4e78-4348-8317-0e1b5d2c122f&cache=v2)
- User A wants to talk to User B.
.png?table=block&id=d3b58993-baf5-45cf-96c2-3065fa70d85d&cache=v2)
- User A retrieves User B’s identity
, signed keys , and signatures from the servers.
.png?table=block&id=8196552f-c408-483d-ace6-eb3f5a8e6bd6&cache=v2)
- User A verifies the signatures to ensure that the identity and keys genuinely belong to User B.
.png?table=block&id=656df631-a5ed-4727-b014-2205ec30d49a&cache=v2)
- User A generates a temporary key
to create a secret key composed of the aforementioned temporary key , User A and B’s identities and , and one of User B’s signed keys .
.png?table=block&id=5b980597-09ea-4f2a-84eb-d50754648d6e&cache=v2)
- User A encrypts an initial message with this secret key and sends it to User B, along with User A’s identity
and the temporary key .
.png?table=block&id=26102e5c-15a7-4200-9ac6-5be5b292a374&cache=v2)
- User B has his own identity (I_B) and the key used by User A (SPK_B), so he can now construct an identical secret key.
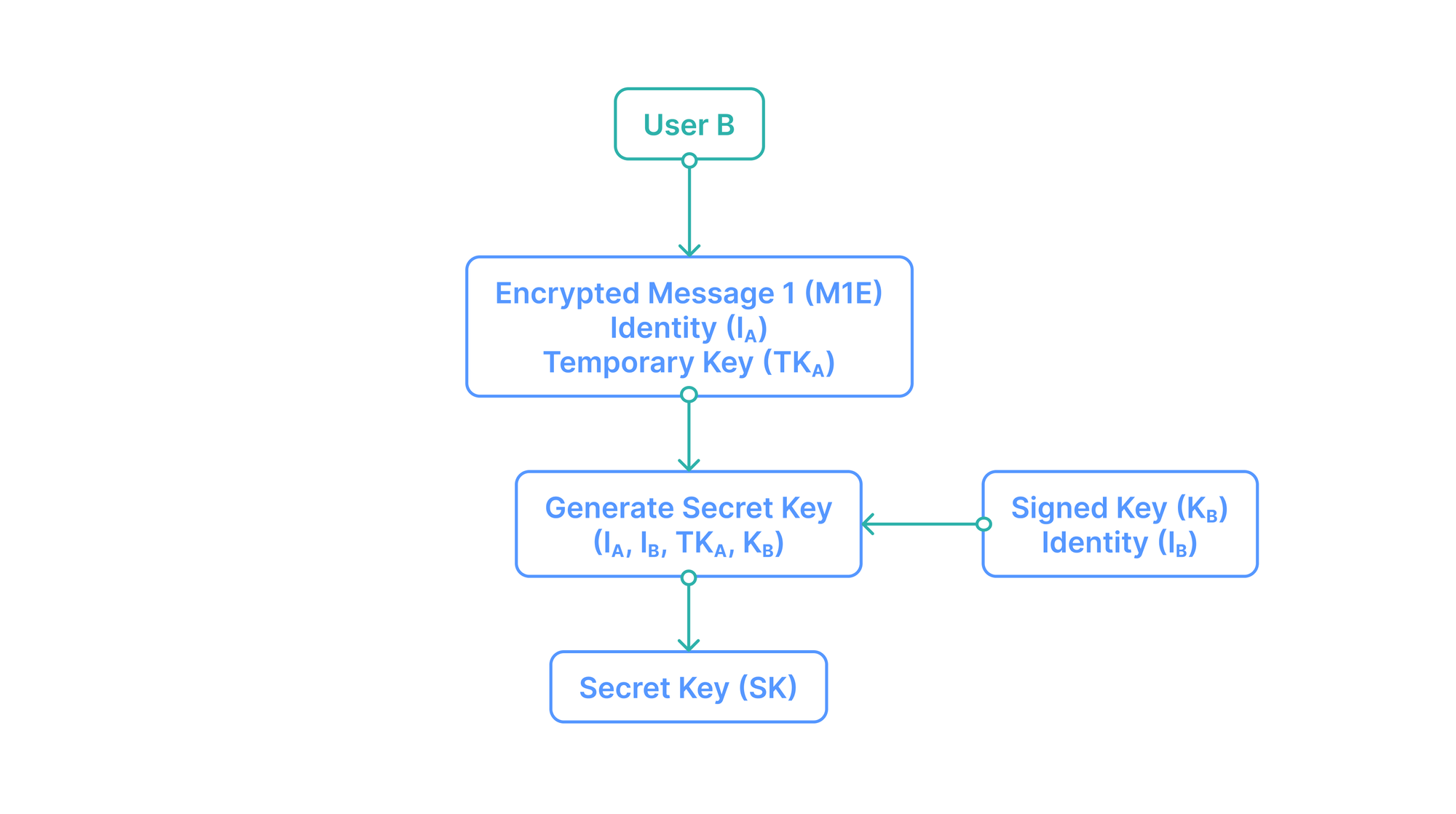
- Both users share the same secret key that can now provide the basis for further communication.
Send and Receive End-to-End Encrypted, Forward Secured Messages (with the Double Ratchet Algorithm)
The Double Ratchet Algorithm provides post-compromise security by encrypting each message with a different key derived from the previous, making a compromised key non-functional for future communication.
- Once two users establish a conversation, they share a secret key that is used to generate two key chains: one for sending and one for receiving.
.png?table=block&id=0165c885-1f44-4d6e-8913-d13db3d1466e&cache=v2)
- When User A sends User B a message, User A’s sending chain generates a key to encrypt the message.
.png?table=block&id=81ce32b7-5f45-400d-a1b6-c313edc6efcc&cache=v2)
- On User B’s side, his receiving chain also generates a key to decrypt User A’s message.
.png?table=block&id=c37f87b7-24e0-429b-b503-fe5066f3bc88&cache=v2)
- This process is continuously repeated, in which each new sending/receiving key is derived from the previous one.
.png?table=block&id=c0ce0aa0-6a2e-46a2-baf2-cb94bbf40a18&cache=v2)
Implement Ready’s Messaging Protocol in a Group Setting
In a group setting, both X3DH and Double Ratchet are applied to every possible pair of users.
- Establish secret keys between users with X3DH.
.png?table=block&id=30a33eda-07ad-4c7a-81ba-72101e71368d&cache=v2)
- Send and receive encrypted messages, pairwise, with Double Ratchet.
.png?table=block&id=e49abce9-1ed7-439d-9127-48f13d124bb9&cache=v2)
